The author Alexander Dore worked in Military Flight Test based out of Edwards AFB and New Naval Stealth Technology out of Pearl Harbor for many years. Dore also worked on the development of virtual manufacturing and embedded security on the F-32 Joint strike Fighter (JSF) development with Dassault Systemes and IBM. Dore also worked with Siemens and Lockheed Advanced Systems developing UML as a forensics language to engage cyber threats through OO Modeling. Dore graduated and received a Masters from the University of Washington Seattle under the Boeing Chair (David Notkin), in advanced OMG Model Driven Architecture in UML, as well as writing a product level thesis interpreting GammaForm Pattern development in Java.
Advanced Persistent Threats or MITRE ATT&CK designated APTs.
The Bad Guys aka Advanced persistent threat(s) (APTs) are identified from the forensic evidence (atomic) of a breach or attempted breach directed by a stealthy enemy actor that directs said attacks (threats) on multiple perceived vulnerabilities; simultaneously and continuously. Worse still, technology defects are traded among APTs centered in Qatar on the Dark Net; classified as Zero Days. APTs are successful because there are often moles already inside the target organization.
These APT actors are typically an enemy combatant nation state, a state-sponsored terrorist group, or merely a malicious entity, that attempt or gain unauthorized access to a computer network or via a paid (bribed) informant. Attacks can be layered, and tool sophistication intensified, based on resistance and often the errant tool remains undetected for an extended period (sometimes a year) of time. In some cases the errant tool is never discovered or able to be placed in quarantine, disabled or destroyed, as it often self-destructs. These sophisticated tools subsequently do extensive damage by acquiring sensitive data, ransoming said data, or disrupting an organization by modifying controls causing havoc.
Without doubt APTs are an ever-increasing threat to National Security
For example we are on the EDGE of WWIII. In the current war in the Ukraine we see two fronts; physical and virtual battlegrounds. Most recently China launched a Spy Balloon and penetrated NORAD, that gracefully floated over the most sensitive military areas in the US unabated till it was shot down in the Atlantic. Low tech outwitting high tech. Ingenious. The high probability is that the Balloon espionage initiative is operated by the Naikon APT27 Group that is tied to China’s PLA Unit 78020 directly under the control of President Xi Jinping. Naikon operates out of Kumming located in Chengdu as the MR Second TRB Military Unit Cover Designator. Naikon APT is also directly linked to cyberespionage activities against US and other ASIAN US supported nations in the South China Sea. A series of geo-political motivated attacks in all probability initiated from converted reefs into islands in the China Sea have been attributed to this APT including diverting a US Destroyer to collide with a Philippines flag container vessel. The group uses advanced hacking tools as in GreenSky27, most of which are developed externally (Iran), and include full-featured backdoor and exploitation builders, as well as deploying remote admin tools (RAT) that downloads additional malware and instruction sets to take over controllers typically in the Microsoft Stack.
MITRE ATT&CK reported that FireEye identified The Chinese People’s Liberation Army (PLA), Unit 61398 as APT1, also designated as Comment Crew, Comment Panda, TG-8223, Group 3, GIF89a, and Byzantine Candor. APT41 aka Winnti, Barium and Wicked Panda is another prolific Chinese intelligence asset dealing mainly with financial crimes especially blockchain penetration. APT 31 is a China-nexus cyber espionage actor focused on obtaining information that can provide the Chinese government and state-owned enterprises with political, economic, and military advantages. Part of the APT27 Naikon group is team Lucky Mouse aka Iron Tiger, Bronze Union, and Emissary Panda is another Chinese threat group specializing in spear-phishing attacks. In conclusion China has weaponized vast resources spending billions of dollars on the largest adversarial APT Group far outreaching the US, Israel, and Europe combined.
The Chinese have built their PLA cyberwar command and control by deploying 80% of its resources in attacking the US, the remaining 20% being defense oriented, whereas the US is investing 80% of its NSA and military resources on defense, as the US is not only threatened by China, but North Korea that uses its highly effective APT Lazaus to target the US literally stealing our top secret nuclear technology to support their globally appropriated arsenal. Additionally Iran has a huge cyber attack force consisting of APT33, APT34, and APT35, segmented into different targeting vectors. APT 33 attack vectors specialize in spear-phishing; APT 34 attack vectors specialize in targeting a broad industry spectrum including government, energy and telecommunications; whereas APT35 specifically targets the military industrial complex, especially military aerospace and drone technology. This is evident as Iranian drones sold to Russia are playing a huge part in the technology war over the Ukrainian theater.
Lastly Russia is also a huge player and utilizes 5 major APTs to do its dirty business disrupting the Free World. APT28 and APT29 are forefront as well as state sponsored groups Berserk, Venomous Bear, and Sandworm teams. Different to China, NOKO, and Iran, Russia in its westernized wisdom outsources a lot of its espionage infiltration technology to high quality Russian vendor science labs and universities that compete producing innovation that slow moving military and bureaucratic government agencies are unable to deploy. Plus they are nimble and hard to locate as they constantly move to avoid detection. Totalitarian regimes like China, NOKO, and Iran use brute force to inspire their hackers; as in punishment and even death for low performance.
The Chinese, in their 7,000 year accumulated wisdom, have now initiated a newly found physical means to use an on-and-off shore cybersecurity death star balloon or angry Panda; in that the same balloon technology could transport biological weapons or scorched earth bombs and wipe out the entire US population from about ten balloons. This is the most serious incursion of US sovereignty to date. Only ground radar could perceive its existence, in a narrow aperture of surveillance, based on the earth’s curvature. Satellites couldn’t see it because they are programmed to see planes and missiles.
Instead of operating a cyber attack hub from an underground bunker, the Chinese floated their cyber lab over our heads. I hate to admit: Brilliant and Simple. The mode and effectiveness of the Chinese cyber penetration is yet unknown. Not only did they penetrate our space in full view we were unable to jam the transmissions that breached and penetrated our networks of our entire DHS critical infrastructure.
The damage to national security is irreparable. Parenthetically, the APTs that attack us every microsecond also demonstrate how out of touch our Cybersecurity leadership is in the US and how unprepared we are to defend ourselves from annihilation. Ten, twenty, one hundred thousand CISSPs are not going to save our nation; that’s for sure. In short everything we have created to counteract cyber terrorism has failed miserably.
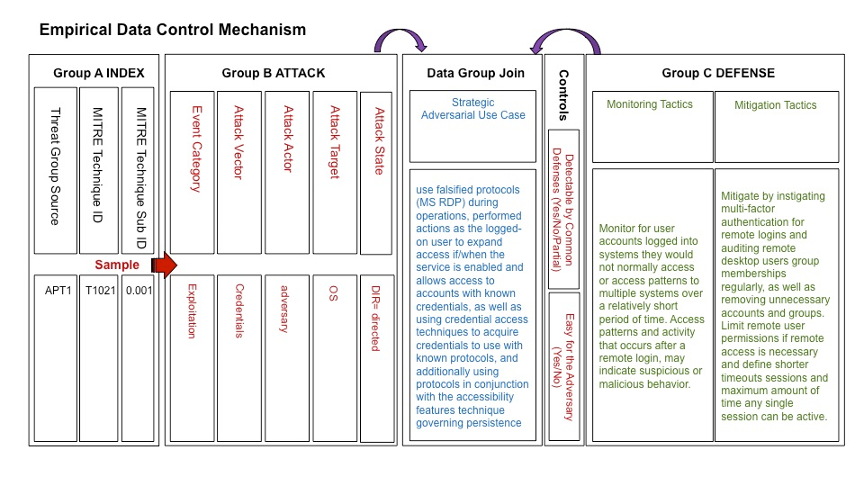
We need the American Genius that fueled our peaceful space race. MITRE ATT&CK is a stimulus for genius and an educative stimuli. The black and white checkered warning flag has been waving in the faces of our public sector, government, and military sectors for years. It is time to wake up and realize this is the greatest threat to the free world since WWII. The US has become complacent and endangers itself. I strongly recommend that those who read this blog aqaint themselves with the data contained in MITRE ATT&CK. I found it mind-boggling. I immediately deciphered how to use the data. Its not obvious. I created a template above to arrange the data to create useful use cases to analyze the data presented in many different views and formats. It’s a slog but I was able to increase my intelligence to add huge IP into my threat modeling that can influence the cyber forensics to harden any system.
I continue to stress that Cyber Practices are at an all time low and outnumbered in expertise by 100 to 1, especially by DevOps. The Cybersecurity Tools, API, and Cloud infrastructure market place is saturated, misleading, and full of bogus even criminally defective products. The cyber/ransom marketplace is driven by fear not common sense. Too much faith is placed on NIST which really only categorizes the damage done into pleasant pigeonholes. All it tells you is how bad it really is out there, but it does nothing to defend our infrastructures and data, it merely tells you what you might need to do, if you can even interpret the forensic damage. Too little too late in my book. Then there is the plethora of Cyber security certifications and low budget diplomas offered online or in community colleges, basically at the educational level of a paralegal or criminologist assistant. It’s a money making sham and our Nation is in Distress from this Clear and Present Danger of proliferating Trumpian Universities.
Not to be overtly repetitious, but based on the current US educational cyber standards we are just learning about unexplained examples of our disastrous failures to halt cyber crimes. We continue expanding our technology attributes with an indescribable GAP of knowledge, as well as understanding the absence micro level substance of what we can discern about the huge errors committed that leave no traces. We are left with no feasible road maps to cure what ails IT in the present or the future. In other words we are clueless. In many cases MITRE data cannot discern as to how or where the damage was done. Maybe a shell was overwritten or penetrated? In short we continually build systems and features that we are unable to diagnose in the event of an attack, or to discover the plethora of maladies that attack them. We are no better at diagnosing and curing cancer in the human body system. We are close but the real cure eludes us. We have interpreted the human genome we employ Crisper to build an mRNA vaccine to abate not cure COVID in its many variations and mutations, but again we only get to the edge. Basically this is because we have erroneously circumvented architecture and handed over the leadership to DevOps. In other words the Blind leading the Blind. Zero Big Picture. Medical science applicabilities have put Computer Science cyber eradication in the shade. In my days in military flight test DARPA addressed the balance or weaponization and curative science. Seriously our US government irrespective of party needs to step up to the plate.
In all consciousness we are not learning the ART of WAR or becoming SEALs and Marines in IT. These CISSP like certifications are equivalent to a boot camp. Its like you give a civilian two weeks to be battle ready. Look at the Russians throwing criminals and conscripts to an early grave with about a two-week survival rate. When I was in Clandestine Services in Angola 70/71 I saw 17-year-old Portuguese conscripts slaughtered in a matter of days after entering the theater of war.
It wasn’t until Obama’s last and eight year that he identified and decried the need to address cyber threats. The NSA has built a 40,000 strong Cyber hub to combat this cyber pestilence. Where were these guys in all the recent government attacks and a Chinese Cyber Espionage Balloon floating over their heads?
So far, everything except MITRE ATT&CK and the NSA Common Criteria 3.1 Methodology (I will address this in another blog), are the only true defense levels that even address the required minimum level of intelligence and weaponization, to at least have a chance to counter attack and decapitate our cyber enemies.
Today, after witnessing the successful Chinese Balloon attack the US must abate the infectious malaise and complacency in the corridors of our government and immediately raise the standards of education addressing cyber war crimes to the level it really deserves. In addition we must influence and turn around the current complete disregard by industry leaders to understand the depth of computer science required to counteract this virtual plague in their worn out engineering that peaked 20 years ago that force the private sector to live in a perpetual legacy state.
First off we must recognize and accept that there is NO cybersecurity; period.

